The Terminal 3 (T3) Platform is a comprehensive solution that enriches, secures, and provides privacy-preserving access to user data. Our platform operates through a three-step process designed to ensure data integrity, user privacy, and regulatory compliance.
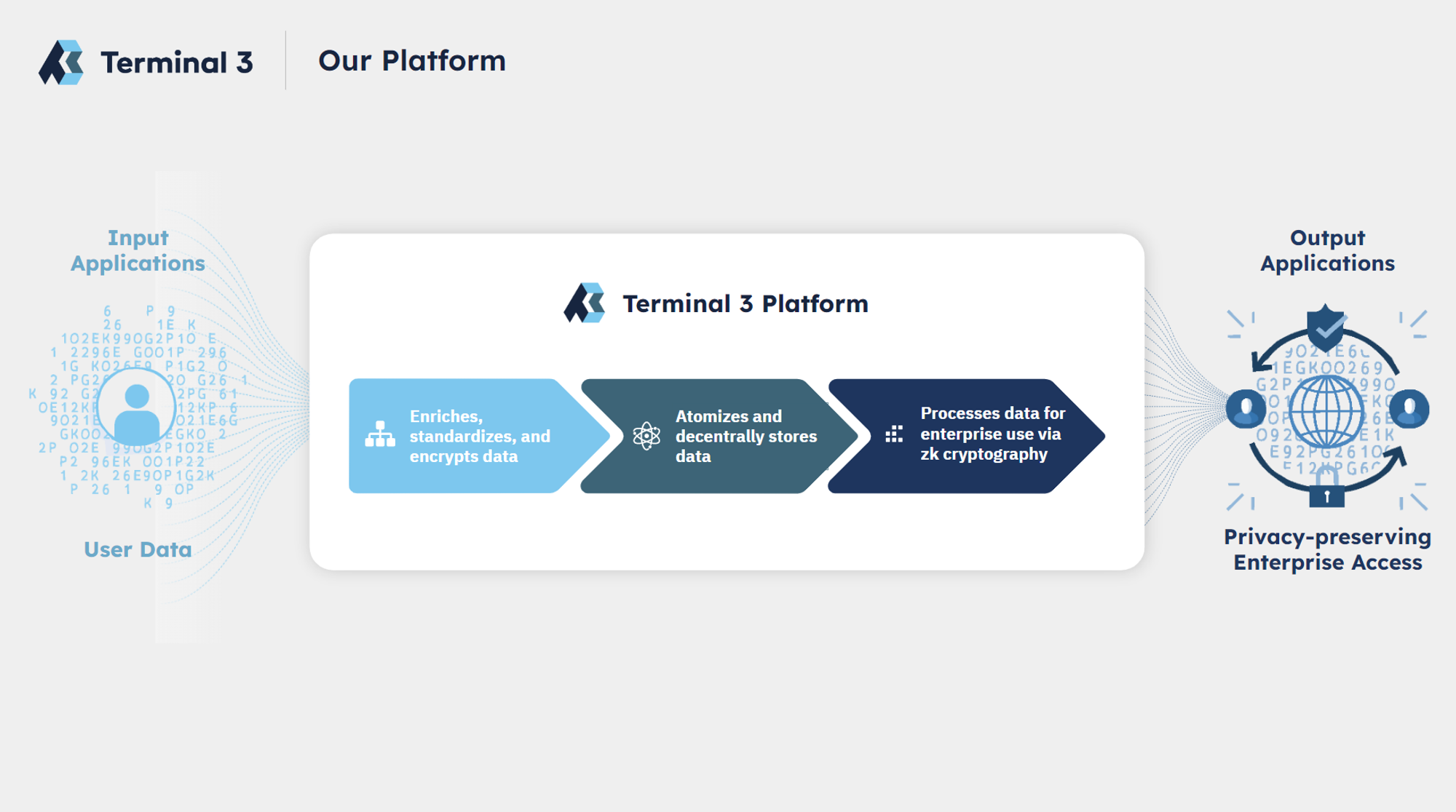
1. Enrich, Standardize, and Encrypt User Data
Before user data is sent to the Terminal 3 platform:
- Client-Side Encryption: Private data and access control conditions are signed and encrypted client-side using symmetric key encryption.
This ensures data remains secure and under self-sovereign user control.
- Decentralized Key Storage: Encryption keys are stored in a decentralized key management network.
Once received by Terminal 3:
- Decryption for Processing: Data is decrypted as necessary using the Terminal 3 signature for processing.
- Data Enrichment: With user consent, data is enriched with both on-chain and off-chain data.
- Standardization: Data is transformed to a standardized schema, enabling interoperability across Web3 platforms.
- Optimization for Segmentation: Prepared data allows for advanced user segmentation.
- Cryptographic Data Commitment: Before storage, a cryptographic commitment is made on-chain.
- Verifiable Credentials Generation: Verifiable credentials holding metadata of underlying identity claims are generated as needed.
2. Atomize, Catalog, and Decentrally Store User Data
After processing:
- Re-Encryption and Atomization: User data is re-encrypted and broken into smaller chunks.
- Decentralized Storage Network: Data chunks are saved across a decentralized storage network.
- Secure Reference Storage: The content ID (CID) of each data object is stored on Terminal 3 in a secure reference data store.
- Tamper-Proof and Immutable: This approach ensures data integrity and immutability.
- Privacy Assurance: User data and personally identifiable information (PII) are never stored on-chain.
- Self-Sovereign Ownership: Decentralized storage grants users self-sovereign control over their data.
- Regulatory Compliance: Our methods adhere to data protection and privacy regulations.
3. Privacy-Preserving Data Access via Zero-Knowledge Cryptography
When enterprises wish to learn about their users:
- Zero-Knowledge Proofs: Use our enterprise applications secured by zero-knowledge proofs.
- Audience Segmentation: Create user segments based on specific criteria (e.g., “users older than 25 living in Hong Kong”).
- Email Campaigns: Send targeted communications to audience segments.
- Secure Query Engine: Securely processes requests and returns a count of matching users.
- Data Privacy: No underlying identity information (e.g., birth dates, email addresses) is ever revealed.
- Verified Data Integrity: Enterprises can trust the data is verified and untampered, thanks to zero-knowledge proofs.
By following these steps, the Terminal 3 platform ensures that user data is
handled securely and privately, while providing enterprises with valuable
insights—all without compromising user trust or regulatory compliance.
