Join the waitlist to get early access to the
Terminal 3 Network, launching in 2025.
-
Privacy-enhancing technologies (PETs) to enable secure data storage and processing:
- Threshold Encryption: all data is encrypted with threshold encryption. This cryptographic method requires multiple parties to cooperate to decrypt the data; no single party can decrypt it alone. A certain threshold of parties (e.g. 6 out of 10), must combine their decryption keys or shares to unlock the encrypted information. Even if one node is hacked, the data remains secure and is not exposed.
- Homomorphic Encryption: this cryptographic method allows computations to be performed on encrypted data without decrypting it.
- Trusted Execution Environments (TEEs): secure computational enclaves within processors that deliver enhanced security beyond conventional operating systems. These isolated environments safeguard sensitive data and critical code. They effectively shield them from unauthorized intrusion or manipulation by other software on the same device. By establishing a protected processing environment, TEEs maintain data confidentiality and integrity. This ensures that even if the broader system is compromised, the most critical information remains safe.
- Zero-Knowlege Transport Layer Security (zkTLS): enhances traditional TLS for secure and private data transfer with multiple parties. It allows secure communication and adds zero-knowledge proof capabilities, so data and identities can be verified without revealing the actual data.
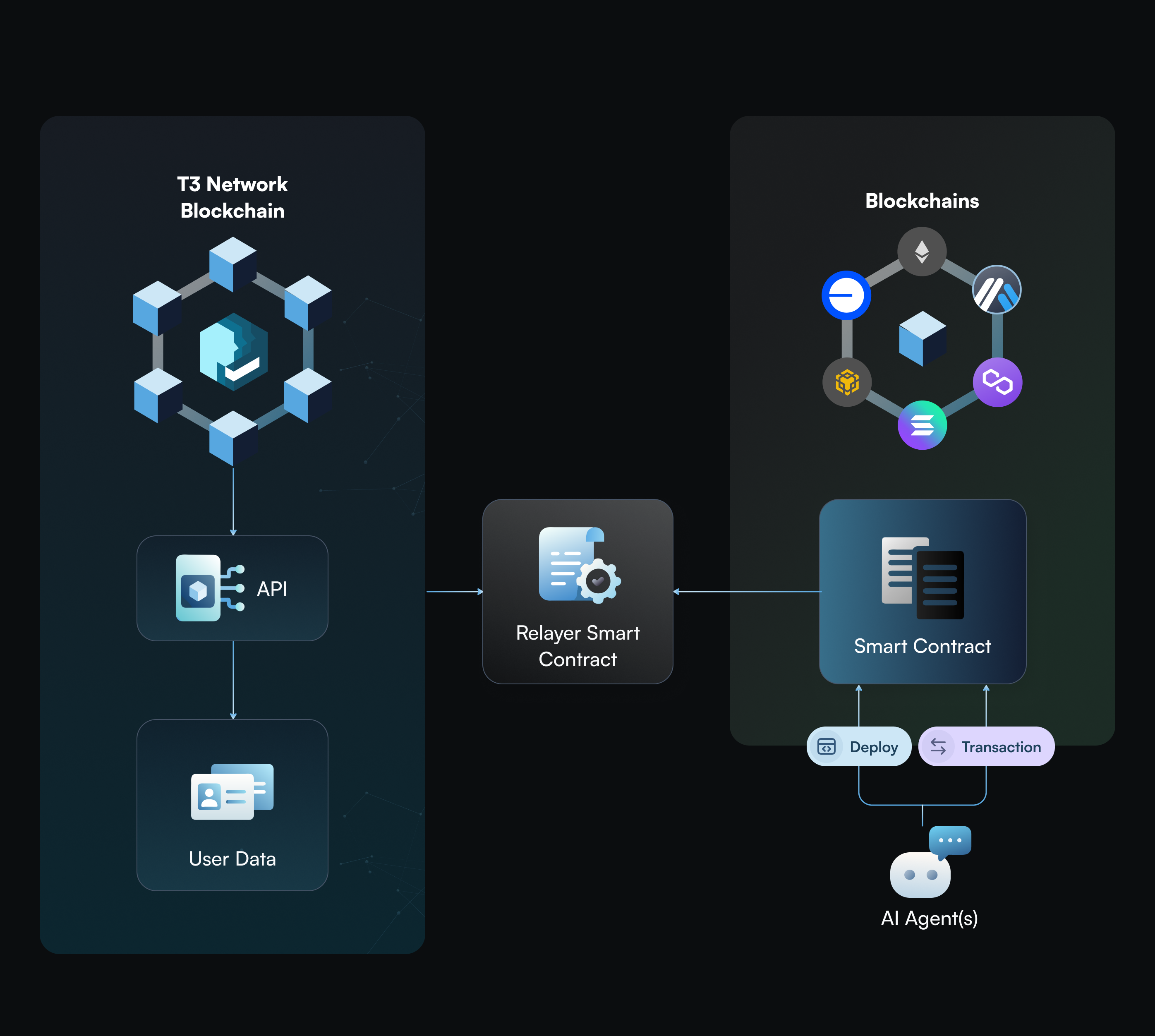
- Relayer Smart Contract: bridges supported blockchains and T3N network, enabling smart contracts on supported blockchains to access T3N data and services. For example, an AI agent request would first call its AI agent smart contract (i.e., application logic). The AI agent smart contract would then forward the request to the T3N Relayer Smart Contract (Figure 5). Upon the T3N event listener receiving the request, T3N would start processing the request, and subsequently register the result back on the originating chain through the T3N Relayer Smart Contract.
-
T3N Chain: supports different levels of application code privacy in two stages:
- Stage 1: The T3N Chain is an authorized blockchain designed to manage shared resources across the entire T3N network. Its functions also include supporting node operator staking and governance. However, the chain does not provide an open execution environment for running smart contracts. At this stage, both AI Agent smart contracts and the T3N Relayer Contract are deployed on public EVM blockchains, which means that AI agent smart contracts and T3N Relayer Smart Contract are public.
- Stage 2: The T3N Chain will support smart contract deployment. This allows AI Agent smart contracts to be deployed on the T3N authorized blockchain, ensuring their application code remains private.
-
Universal Last Mile API Connector: The T3N Universal Last Mile API Connector helps applications and AI agents provide private user data (e.g., PII and payment information) to transaction platforms (e.g., booking.com) without exposing the data to those applications or AI agents. T3N supports two types of Last Mile API integrations:
- Public API integration: T3N curates a whitelist of secure public APIs for applications to consume. Any API not on the whitelist requires user approval before an application or AI Agent can access it.
- Pre-authorized API integration: T3N pre-integrates with commonly used transaction platforms that require pre-authorization from the transaction platforms (e.g., booking.com).
- Universal Data Storage Connector: The T3N Universal Data Storage Connector gives data owners and developers the ability to select their preferred storage solutions (e.g., IPFS or T3N’s default) based on their individual preferences.
-
Verifiable Credential (VC) SDK: T3N Verifiable Credential SDK provides VC issuers and verifiers with the essential tools to quickly issue and verify W3C standard VCs. T3N VC SDK also provides the additional key features to standard W3C standards VCs (aka Smart VC):
- Support easily refreshable VC (NOTE: the majority of VCs today are static.)
- T3N VCs are encrypted, and VC data can be verified without exposing it.
- T3N supports two types of selective disclosure:
- Allowing users to choose which data fields to share
- Obfuscating specific data within a field.
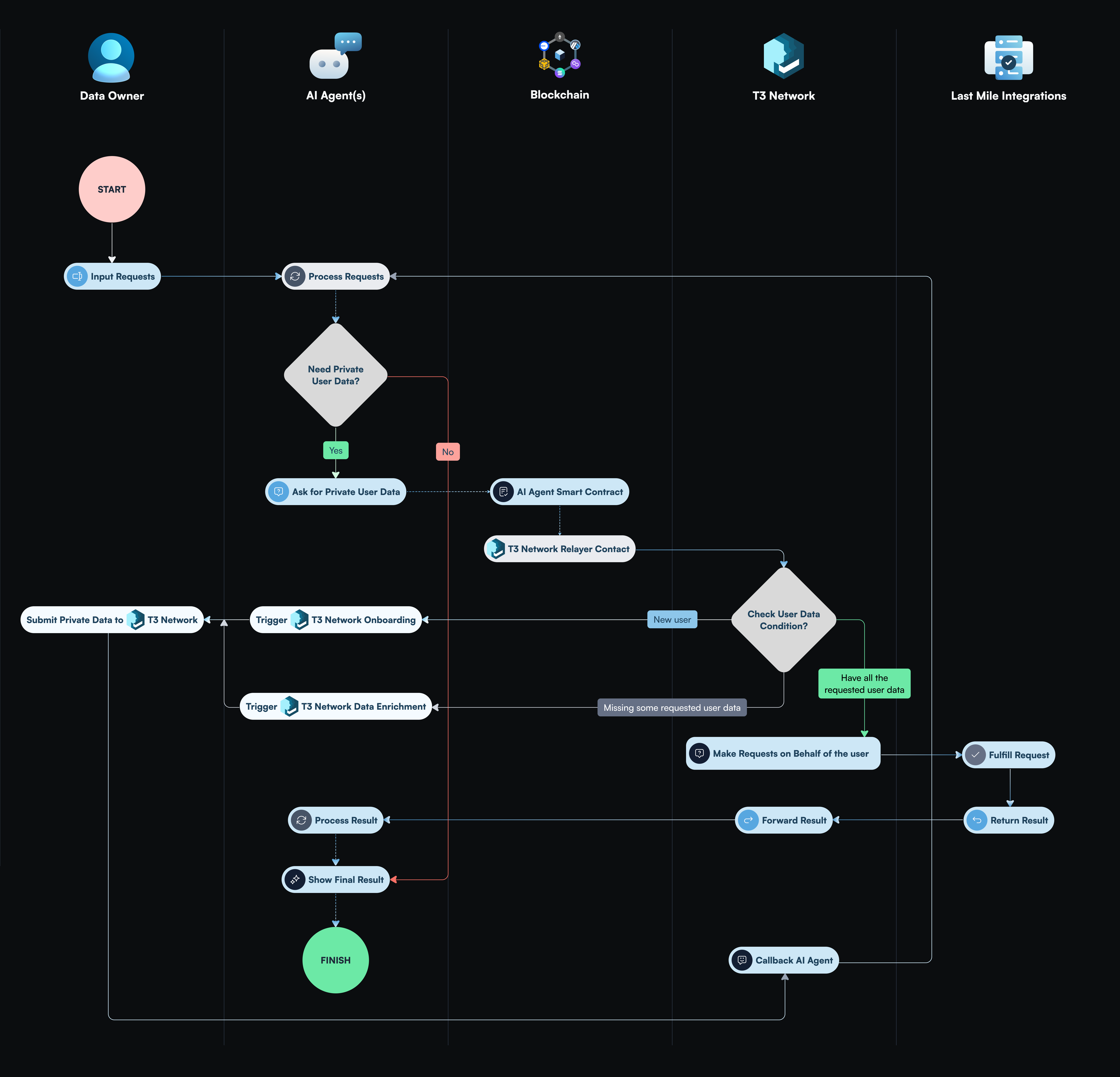
- Stage 1 - Both AI Agent smart contract and T3N relayer contract are on public EVM blockchains.
- Stage 2 - AI Agent smart contract can also be deployed on T3N authorized blockchain.