Join the waitlist to get early access to the
Terminal 3 Network, launching in 2025.
- Phase 1: Decentralized private data - Ensure safe and private AI agents.
- Phase 2: Proof of human and AI agent data layer - Establish a trusted oracle for verified humans and AI data.
- Phase 3: Trusted data economy - Enable users to monetize their verified data securely and fairly.
Users
The players in the T3N ecosystem are as follows:- Developers - Developers who build AI agent applications.
- Data owners - Owners of private user data.
- Data providers -Data providers are the entities that supply user data into the decentralized user data vault. Data providers are typically data owners themselves; however, they can also be any third parties granted consent by data owners.
- Data consumers -Data consumers are the entities that utilize user data from the decentralized user data vault. These consumers are typically required to compensate data owners for accessing their data.
- Node operators -Node operators maintain the infrastructure of the decentralized user data vault.
- Compliance authorities - Compliance authorities are entities tasked with ensuring that organizations adhere to relevant laws, regulations, and industry standards. These authorities typically include both government-established regulatory agencies and industry-specific bodies.
- Verifiable credential (VC) issuers - Verifiable credential issuers are entities that issue digital credentials that can be verified independently.
- VC verifiers - VC verifiers are entities that validate and verify the authenticity and trustworthiness of VCs.
Phase 1: Decentralized Private Data
Goal: Ensure data privacy and security when using AI agents Primary users- Developers (and applications)
- Data owners
- Online financial product applications (credit cards, personal loans)
- Insurance claim management
- Customer support interactions
- Job searching tasks
- Patient registration
- Online shopping
- Securely stores user data encrypted in a decentralized manner;
- Provides access to private user data via privacy-enhancing technologies (PET); and
- Delivers user data to third-party integrations (i.e. last mile data delivery) where only the intended recipient can view the data without the ability to link it back to anonymous identities.
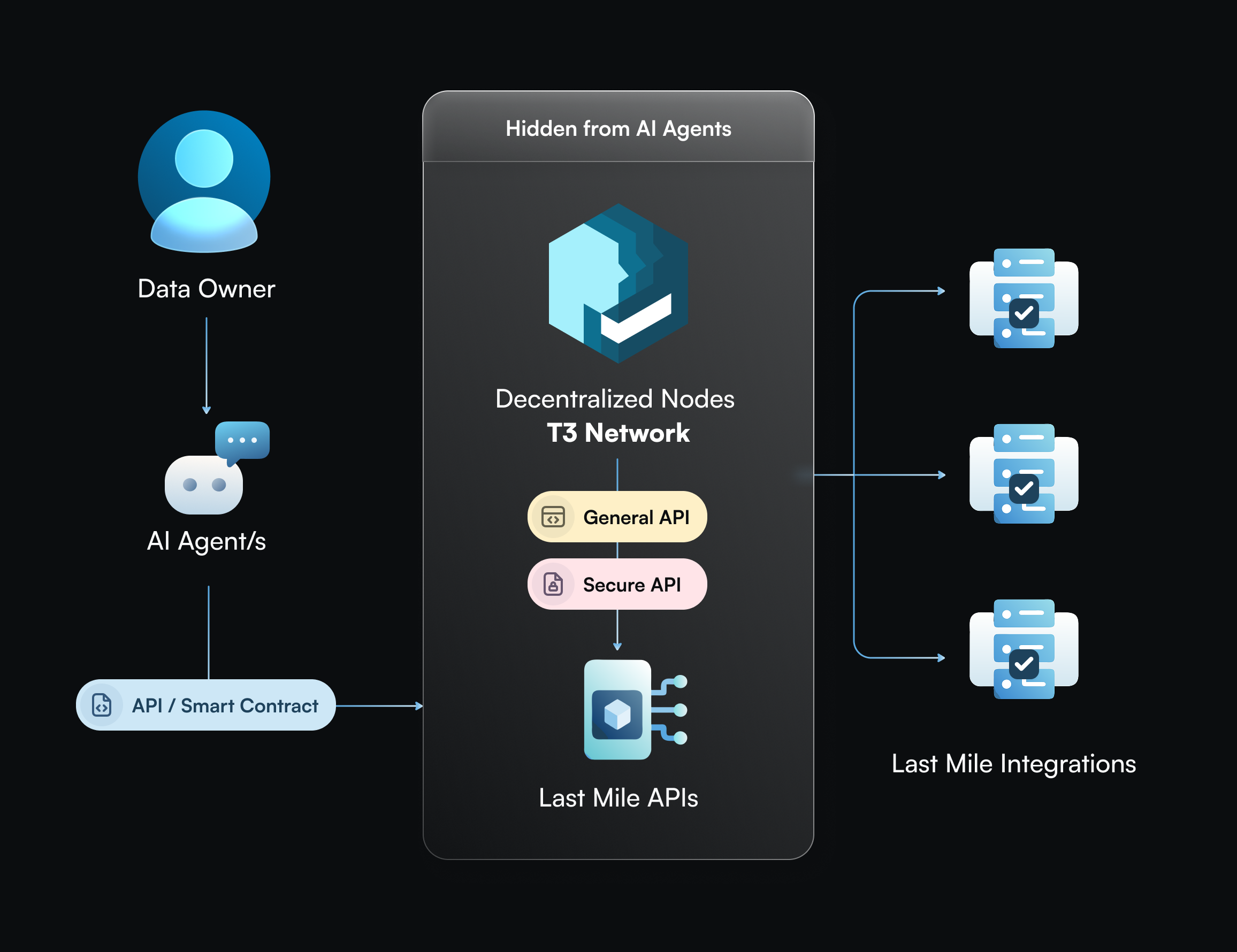
Interacting through an AI agent
AI agents, such as computer-using agents (CUA), are often used to automate specific tasks for their human operators. For instance, AI travel agents can make flight and bookings, while AI crypto trading agents can execute trades. T3N assists these AI agents in connecting with an ecosystem of third-party integrations via API or smart contracts, and conducting last mile delivery of private data necessary to complete transactions. This ensures that AI agents never have access to sensitive information, such as PII, API keys, or private keys. Other key highlights include:- T3N does not interact with data owners directly.
- Data owners may be onboarded during the process if they do not yet have a T3 account
- T3N performs critical verifications:
- Requests are from authorized agents
- Safe URL (i.e. whitelisted or user approved URL)
- Fund amount (if there is any via Secure API)
- All transactions and API calls are recorded and auditable.
Interact directly
Data owners can directly interact with T3N to manage data through a user interface to enrich their user data and manage their data token for future data consumption (Figure 2). A data token is a user-signed data access token that grants specific permission to disclose selective user data to the token holder. The data token can be single- or multi-use, and is non-transferable. This direct interaction with T3N allows data owners to enrich their data and properly configure their data tokens in advance, enabling them to take full advantage of automation when interacting with an AI agent.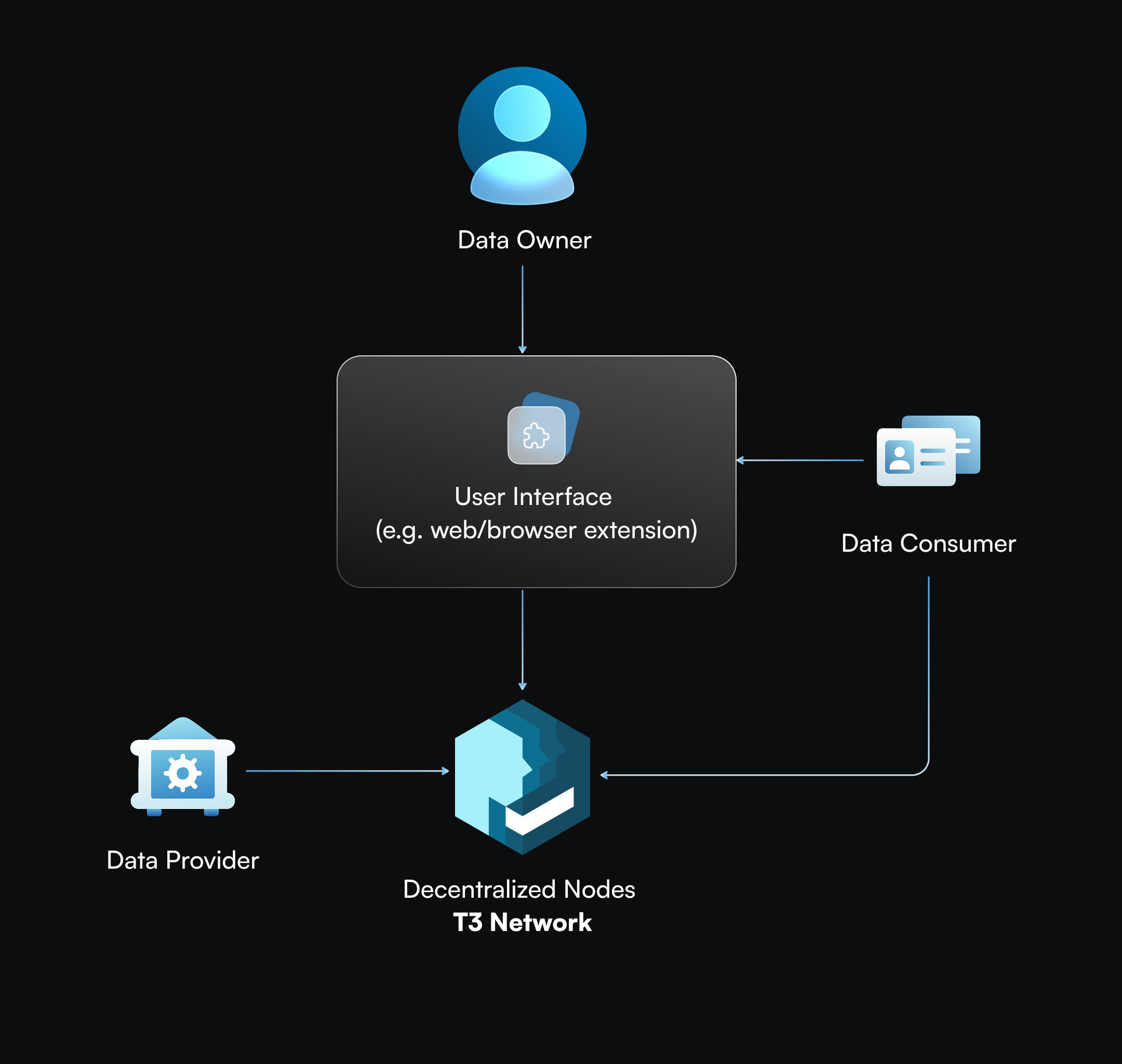
Phase 2: Proof of Human and AI Agent Data Layer
Goal: Establish a trusted oracle for verified human and AI data. Primary users- Verifiable credential (VC) issuers
- VC verifiers
- Data owners
- Compliance authorities
- Reusable KYC information
- Proof of accredited investor qualification
- Academic degrees and professional licenses
- Loyalty program membership
- Vaccination records
Phase 3: Trusted Data Economy
Goal: Enable users to monetize their verified data securely and fairly Primary users- Data owners
- Data providers
- Data consumers
- Data monetization
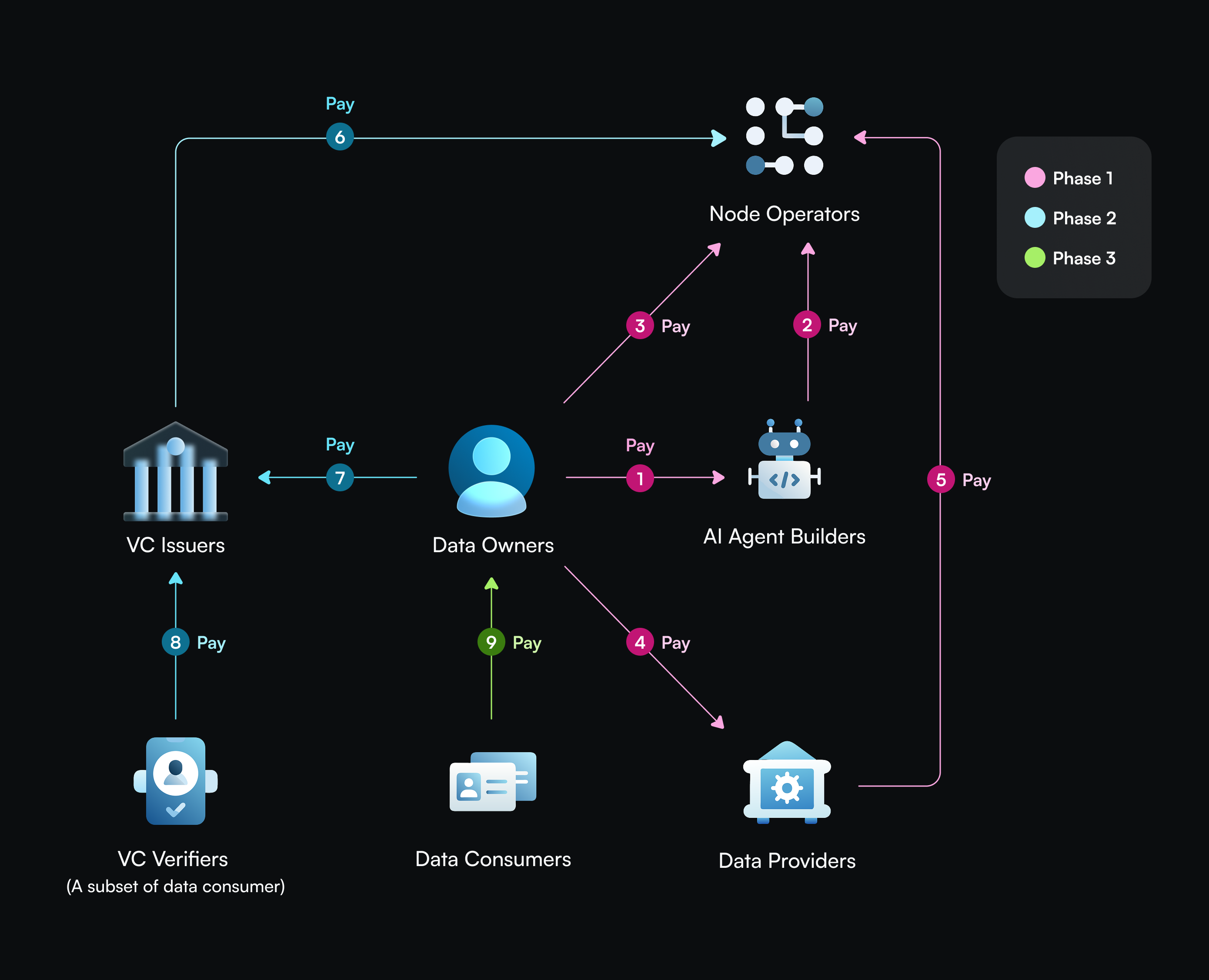
- Data owners pay AI agent builders for personalized AI services.
- AI agent builders, on behalf of data owners, pay node operators for data storage and processing.
- Data owners pay node operators directly for data storage and processing.
- Data owners pay data providers for their data population services.
- Data providers, on behalf of data owners, pay node operators for data storage and processing.
- VC issuers pay node operators for VC storage and processing.
- Data owners pay VC issuers for VC issuance.
- VC verifiers pay VC issuers for VC verification.
- Data consumers pay data owners for accessing their data.