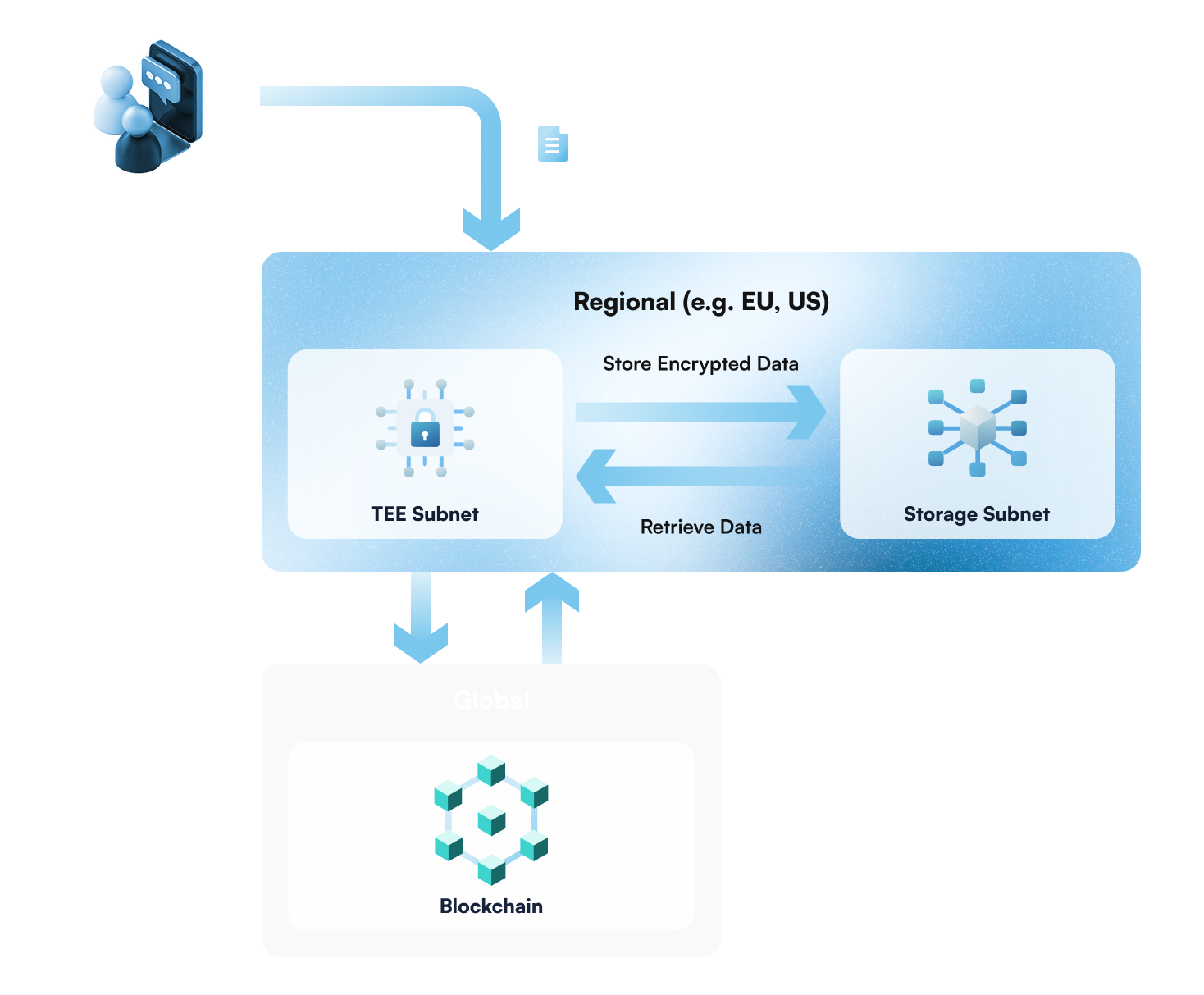
Regional Secure Compute and Storage With Global Auditability
Data within Regional Subnets can never be accessible or processed by other Subnets without explicit user permission.
1. Trusted Execution Environment (TEE) Network
The TEE Network serves as the entry point and central processing core. All computations are performed inside the secure computational enclaves within processors that deliver enhanced security beyond conventional operating systems. These isolated environments safeguard sensitive data and critical code. They effectively shield them from unauthorized intrusion or manipulation by other software on the same device. By establishing a protected processing environment, TEEs maintain data confidentiality and integrity. This ensures that even if the broader system is compromised, the most critical information remains safe.T3N TEE Network currently utilizes Intel TDX (Trust Domain Extensions) to run Secure Encrypted Virtual Machines. Future versions will support other TEEs.
Execution Flow
The TEE node provides a secure execution runtime for TEE Contracts, managing the surrounding execution environment. TEE Contracts define the action logic, while the runtime is responsible for data preparation, authorization checks, and contract loading. Examples- Secure Last-Mile Execution: AI agents perform sensitive tasks—such as booking flights or executing financial transactions—using user credentials injected directly into the enclave, ensuring they are never exposed to the host environment.
- Session Management: Authenticates users via OIDC, passkeys, email, or wallet signatures to establish secure, verified sessions for data processing.
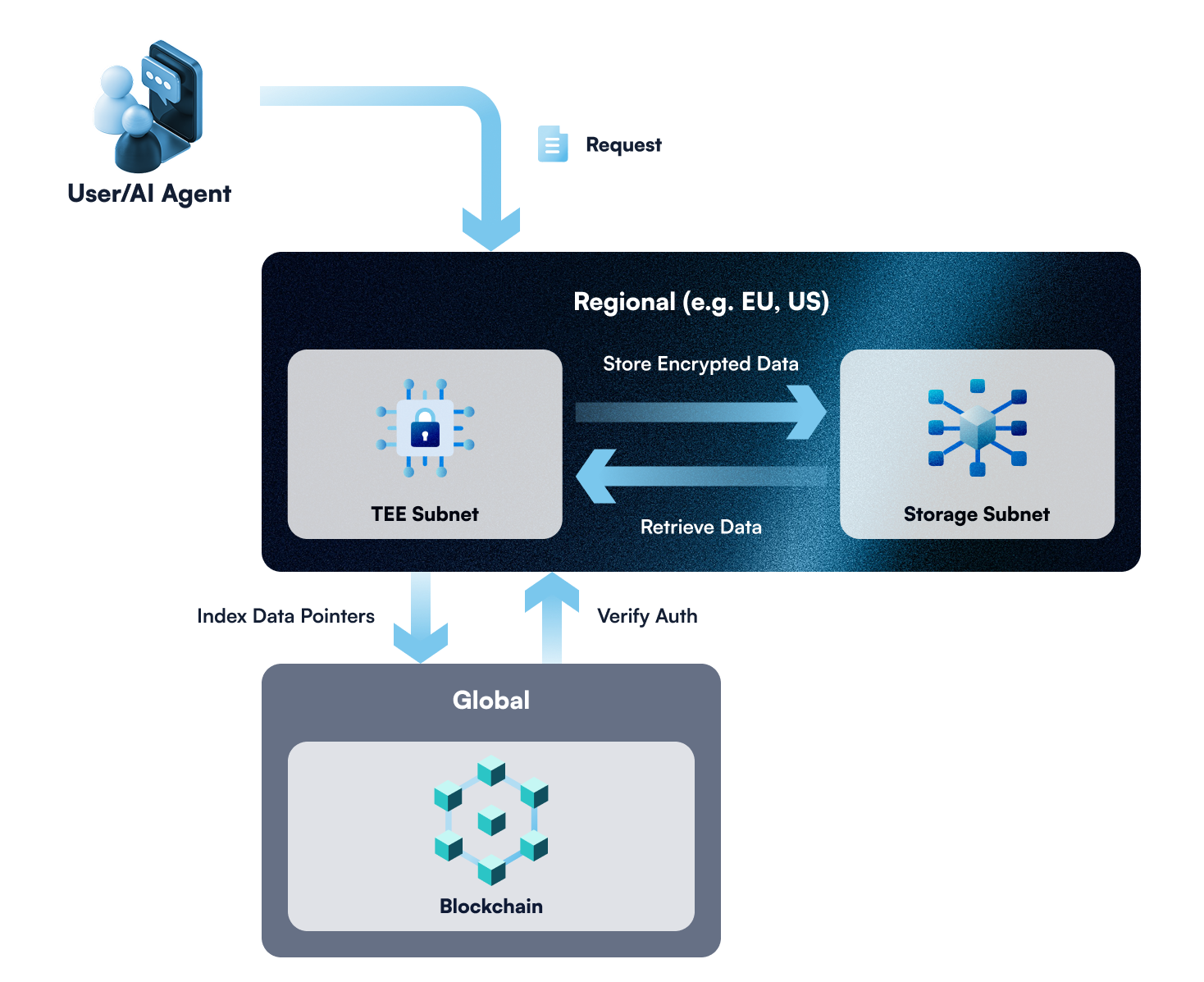
- Request: The TEE takes in a request.
- Decryption: It decrypts PII data using quantum-proof threshold decryption.
- Authorization: It checks with a blockchain runtime (e.g., Substrate pallet) that the requester is pre-authorized to deal with the data.
- Action: It performs the action defined in the TEE contract, including any necessary HTTP calls. All business logic resides in these contracts.
- Response: Returns a success or failure indicator.
Key Components
- TEE Contracts: Deterministic, action-specific logic executed inside the enclave. Contracts are fetched from decentralized storage (e.g., IPFS) if not already cached, and contain all business logic for the requested action.
- TEE Runtime (WASM): TEE nodes host a secure WebAssembly (WASM) runtime that loads and executes TEE Contracts, handling contract isolation, lifecycle management, and execution control.
- Confidential Computing: All sensitive computation occurs inside hardware-backed secure enclaves. Private data is decrypted only within enclave memory and is never exposed to the host operating system.
- Attestation: Each TEE produces a hardware-backed attestation that proves the integrity of the enclave, the runtime, and the loaded contract before execution.
2. Storage Network
T3N decouples storage from computation. The T3N Storage Network securely stores private data – encrypted – in a decentralized storage network by default. Data owners and developers can use their preferred storage solutions (e.g., enterprise private data storage) based on their individual preferences through the T3N Universal Data Storage Connector.Decentralized Storage
Encrypted user data is stored off-chain on IPFS (InterPlanetary File
System) clusters run by node operators. Content Identifiers (CIDs) act as
on-chain pointers.
Enterprise Private Storage
Institutions can use the Universal Data Storage Connector to keep data
in proprietary databases (e.g., for banking compliance) while still
participating in the network.
All data is encrypted client-side prior to upload, with keys securely managed by the TEE network using threshold cryptography.
3. Blockchain Network
The T3N Blockchain Network provides global access governance and an immutable audit trail, without storing any raw user data on-chain. The Blockchain Network is responsible for the following core functions:- Immutable Logs: All data access requests and operations are recorded on the blockchain.
- Identity Management: Manages decentralized identifiers (DIDs) in accordance with W3C standards, enabling verifiable identities for users and AI agents.
- Access Governance: Enforces on-chain permissioning and delegation policies, allowing users to grant, scope, and revoke agent access in a verifiable manner.
- Data Indexing: Stores cryptographic references (e.g., CIDs) to encrypted data residing in the Storage Network, without exposing underlying data.
- Node Registry: Registers and manages TEE and blockchain nodes, including their public keys and metadata, to support secure coordination and verification across the network.