Reusable verified user data
Currently, data owners must repeatedly provide verified data (e.g., KYC info) whenever they interact with different third parties, both in physical and digital settings (e.g., banks or telecom service providers). For instance, a user opening an account at Bank A must complete a KYC verification. If that user then engages with Bank B, a similar time-consuming and costly KYC process must be repeated. A typical reusable verified user data flow on T3N can look like this:- You (i.e., data owner) store your private user data once in T3N.
- A trusted issuer, a reputable and verifiable organization, issues you a verifiable credential that attests to specific user claims within the credential.
- When a relying third party needs to verify you, you share that credential rather than uploading raw documents again.
- Reusable KYC information.
- Proof of accredited investor qualification.
- Academic degrees and professional licenses.
- Loyalty program membership.
- Vaccination records.
Automate transactional tasks with AI agents
Individual
AI agents are rapidly becoming essential tools for individuals automating complex, multi-step tasks that traditionally required human intervention, such as booking travel or managing financial portfolios. However, for these agents to complete “last-mile” transactions (e.g., confirming a flight booking with a payment), they often require access to highly sensitive user data, like payment details, passport numbers, credential, or API keys. Current systems often require users to grant agents full access to this data, creating significant privacy and security risks. If the agent or the platform it resides on is compromised, the sensitive data is exposed, as seen in the UnitedHealth Group and Middle East call center breaches. A typical AI agent-driven transaction flow for individuals on T3N can look like this:- You (i.e., data owner) store your private user data once in T3N.
- You authorize an AI agent (e.g., a travel booking agent) to perform a specific action (e.g., “Book me a flight to Dubai using my preferred credit card”).
- The AI agent processes the request (e.g., finding the cheapest direct flight).
- When the AI agent is about to initiate the last-mile transaction (e.g., actual booking), instead of exposing the private user data to the agent, the AI agent interacts with T3N, which then securely delivers the required private user data directly to the third party (e.g., the airline’s booking system).
- The third party (e.g., the airline’s booking system) receives the data, completes the transaction.
- T3N processes the third-party response (e.g., from the airline’s booking system) before forwarding it, ensuring any private user data is processed first and not returned to the AI agent.
- Online financial product applications (credit cards, personal loans).
- Insurance claim management.
- Customer support interactions.
- Job searching tasks.
- Patient registration.
- Online shopping.
Enterprise
Enterprises are significantly increasing their investments in AI agents, integrating these solutions into their core business and organizational processes. However, despite the enthusiasm, enterprises face major hurdles and have a strong need for robust solutions to address identity, permission and delegation, data privacy, and auditability challenges, particularly for high-stakes and inter-enterprise applications.B2B procurement
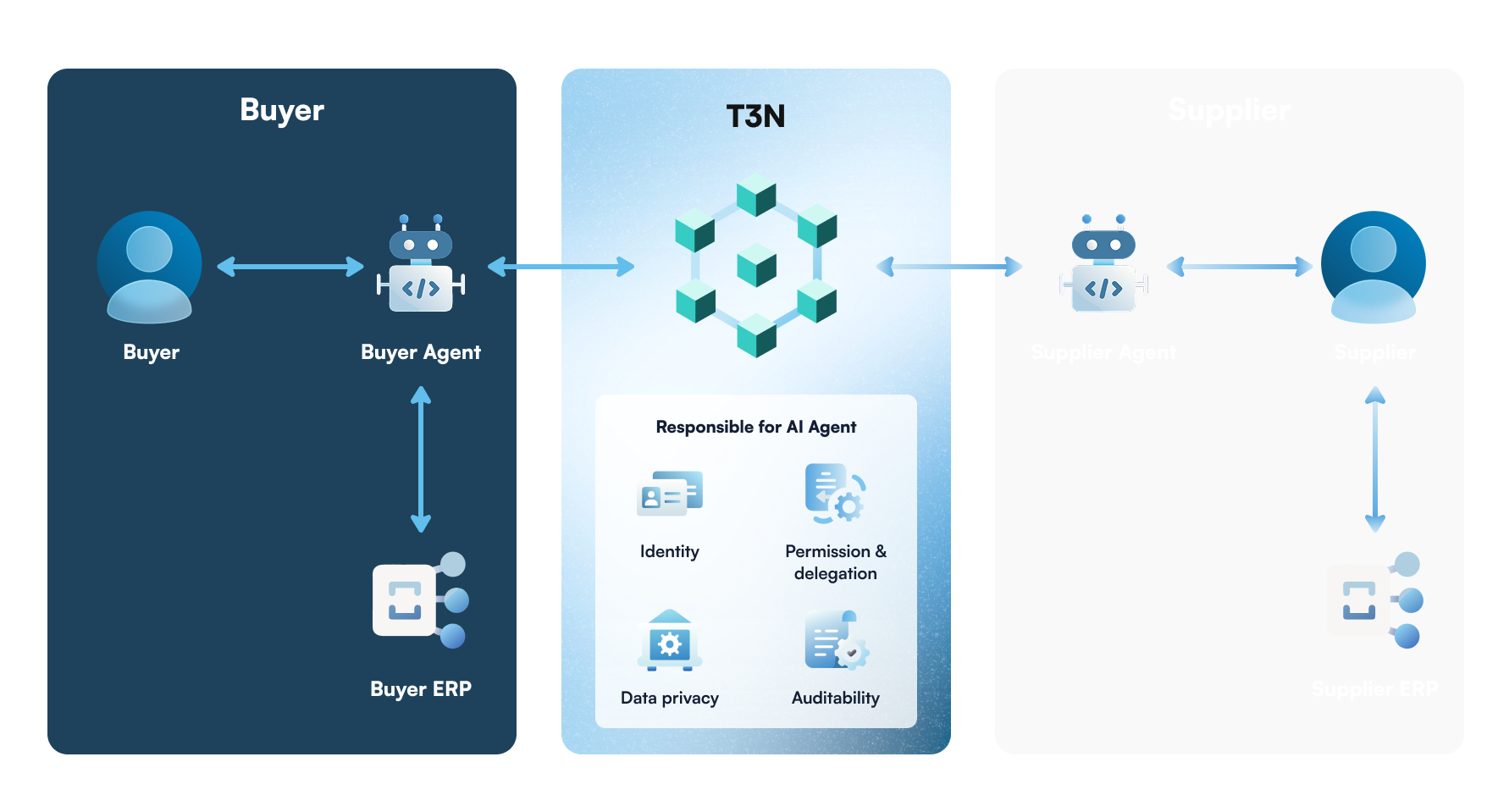
B2B procurement today is burdened by fragmented systems, manual handoffs, and high trust and compliance overhead across enterprises. While core processes such as supplier selection, purchase order creation, fulfillment confirmation, invoicing, and payment are well defined, they remain slow, error-prone, and difficult to automate safely due to data-sharing risks, approval constraints, and audit requirements. An AI agent–driven procurement flow on T3N addresses these challenges by enabling enterprise AI agents to transact on behalf of their organizations under explicit, policy-bound delegation, with secure data custody, verifiable inter-agent communication, and auditable execution across buyer and supplier systems.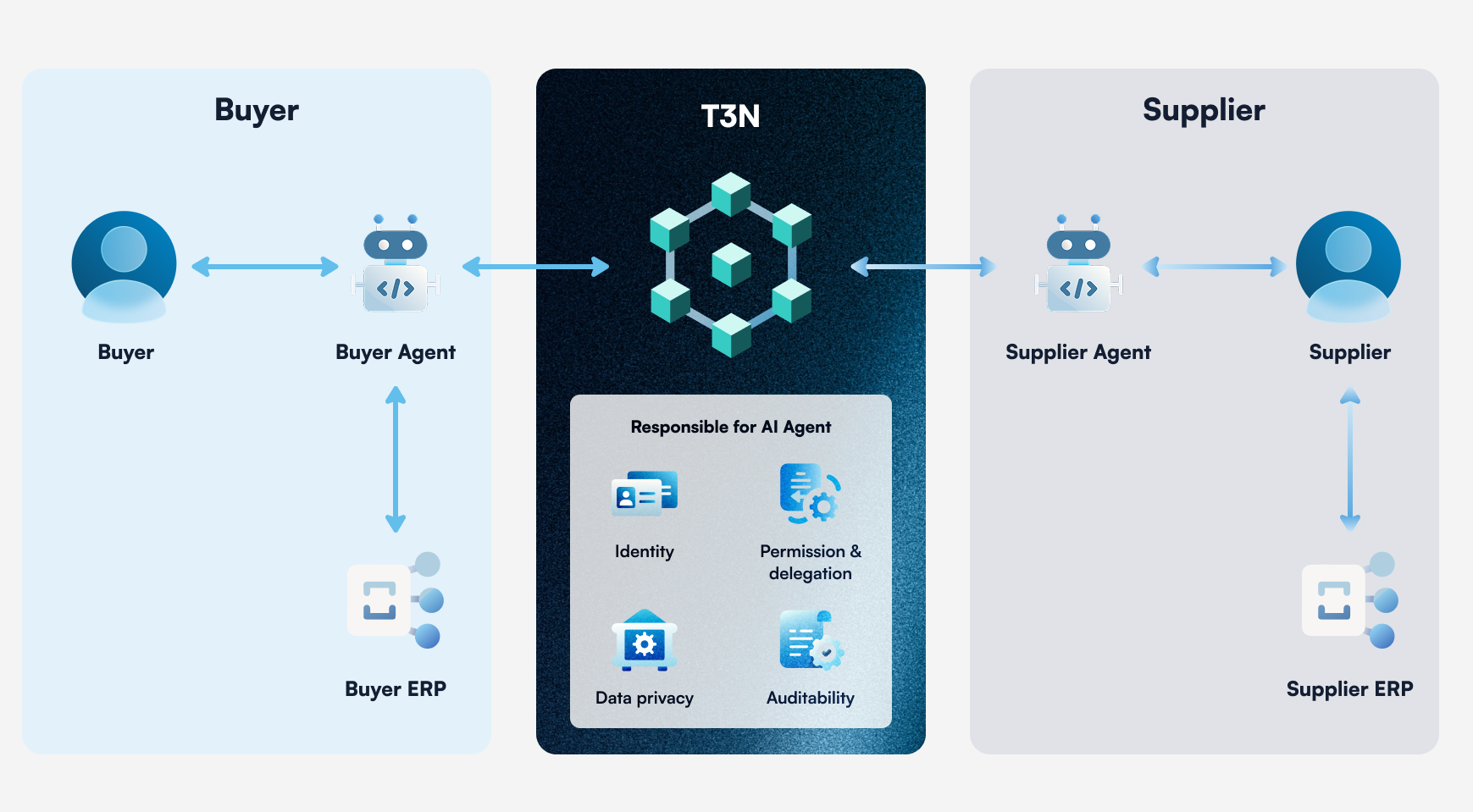
- Enterprise buyer (i.e., data owner) stores its payment info (e.g., enterprise account, stablecoin wallet, or payment gateway key) once in T3N.
- The Enterprise buyer authorizes a Buyer AI Agent to procure goods or services within predefined constraints (e.g., approved suppliers, SKU list, pricing bands, delivery terms, and spending limits).
- The Buyer AI Agent prepares a purchase order (PO) via the enterprise ERP system using pre-agreed commercial terms.
- The Buyer AI Agent sends the PO to the approved Supplier AI Agent via T3N.
- The Supplier AI Agent receives the PO, validates it, and confirms acceptance, delivery schedule, and fulfillment details back to the Buyer AI Agent via T3N.
- Upon delivery, the Buyer AI Agent confirms receipt, and the Supplier AI Agent issues an invoice through its ERP system.
- Before payment execution, the Buyer AI Agent again verifies that the supplier remains approved.
- For the final payment step, instead of accessing payment keys directly, the Buyer AI Agent submits a payment instruction to T3N, which securely delivers the pre-configured payment info to the payment platform or enterprise system.
- The payment platform executes the transaction, and T3N processes and sanitizes the response before returning a confirmation to the Buyer AI Agent and Supplier AI Agent, ensuring sensitive financial data is never exposed to either agent.
Delegate access to human helpers
While AI agents excel at automation, a trusted agent might not always be available for every task. Therefore, temporary and restricted access to a person’s private data or credentials may still be necessary for human helpers, such as personal assistants, family members, or professionals, to complete certain tasks. Current methods, however, often involve sharing the data via email or a chat app (e.g., WhatsApp), which is inherently insecure and risks over-exposure of sensitive information. A typical flow for delegating access to a human helper on T3N can look like this:- You (i.e., data owner) store your private user data once in T3N.
- You authorize a human helper (e.g., a family member) to access necessary private user data to perform a specific action (e.g., “Apply for Thailand Digital Arrival Card”) based on your configurable rules (e.g., single or multiple uses, expiration dates).
- The human helper processes the request (e.g., filling Thailand Digital Arrival Card application form).
- When the human helper requires your private user data, they interact with T3N to access the authorized data (e.g., passport information).
- The third party (e.g., Thailand Immigration Bureau) receives the data, completes the transaction.
- T3N automatically revokes access based on the authorization rules.