- The TEE Runtime is responsible for securely ingesting encrypted data, decrypting it inside the enclave, enforcing authorization, and managing execution.
- The TEE Contract executes the application logic (e.g., check credit score, sign a transaction, issue a verifiable credential) on the decrypted data and returns the result to the runtime for re-encryption and delivery.
Execution Flow & Data Inputs
The contract execution relies on two primary data sources: the parameters from the user’s request and the user’s private data fetched from storage.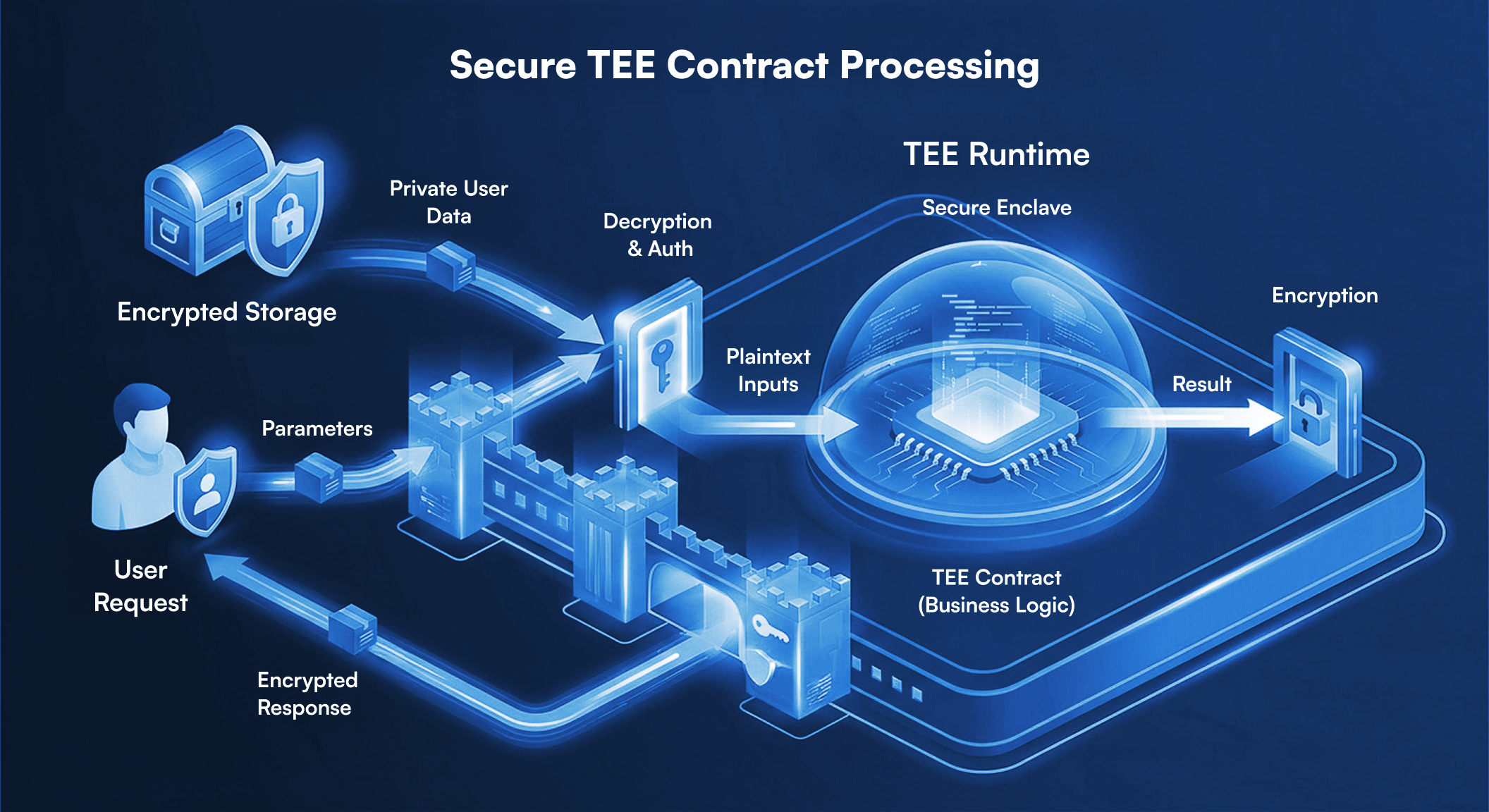
- User Request: Contains arguments for the function call (e.g.,
amount,recipient). - Storage Retrieval: The node fetches the user’s encrypted private state associated with the contract.
- TEE Runtime Processing: The TEE Runtime decrypts inputs inside the enclave, enforces authorization, and prepares the execution context.
- Contract Execution (WASM Sandbox): The TEE Contract runs on plaintext data in a WASM sandbox environment.
- Result: The TEE Runtime encrypts the result inside the enclave and returns the encrypted output to the TEE node for delivery.
- Isolation: Contracts execute in a sandboxed environment with no access to the host file system and no ability to reach arbitrary network endpoints.
- Privacy: Sensitive data is decrypted and processed only inside the hardware-backed enclave; all inputs and outputs remain encrypted outside the enclave boundary.
- Verifiability: Contracts are registered on-chain using immutable content identifiers (CIDs), allowing users to cryptographically verify that the exact code they authorized is being executed.
Capabilities & Host API
To minimize the attack surface, TEE Contracts do not have direct system access. Instead, they interact with the outside world through a strictly defined Host API, implemented using the WASM Component Model, which exposes only explicitly allowed, strongly typed capabilities to the contract.If a capability is not defined in the Host API, the contract cannot do it.
- HTTP Requests: Perform
GETandPOSTrequests to explicitly whitelisted external APIs (e.g., airline booking systems or credential submission endpoints). Contracts cannot access arbitrary URLs. - Crypto Operations: Generate digital signatures and verify cryptographic proofs using keys derived and held exclusively within the enclave.
- Ephemeral Key-Value Store: Read and write temporary execution state scoped to the contract invocation. Stored data exists only for the lifetime of the execution and is not persisted beyond it.
Example Contract Logic (Conceptual)
Security & Sandboxing
T3N uses Wasmtime, a production-grade WebAssembly execution engine, configured with strict sandboxing and resource limits.- Fuel-Based Execution: Each contract invocation is assigned a bounded computation budget (“fuel”), preventing infinite loops and mitigating Denial-of-Service (DoS) attacks.
- Memory Constraints: Hard limits are enforced on memory allocation to prevent resource exhaustion and ensure predictable execution behavior.
- Network Whitelisting: Contracts may only issue network requests to endpoints explicitly authorized in the user’s permission grant or declared in the contract’s manifest. Access to arbitrary URLs is not permitted.
TEE Contract Registry
TEE Contracts are stored in off-chain storage, not stored directly on the T3N Blockchain. Instead, the blockchain maintains a registry of contract references:- Off-chain Storage: The contract’s WebAssembly (WASM) binary is stored off-chain storage (e.g., IPFS).
- On-chain Registry: TEE Contract Registry maps a human-readable contract identifier
tee_contract_name(e.g., booking-contract-v1) to the contract’s immutable Content Identifier (e.g., IPFS CID). - Resolution & Verification: Upon receiving an execution request, a TEE node resolves the CID via the registry, retrieves the WASM binary (if not already cached), and cryptographically verifies its integrity before loading it into the enclave for execution.
Comparison: Smart Contract vs. TEE Contract
TEE Contracts offer distinct advantages over traditional Smart Contracts, particularly regarding privacy and external connectivity.| Feature | Smart Contract | TEE Contract |
|---|---|---|
| Public Binary Code | Yes, onchain | Yes, offchain (e.g., IPFS) |
| Public Source Code | Yes, but centralized (in scanner DB) | Yes, centralized (e.g., GCP Artifact Registry) and decentralized (e.g., IPFS) |
| Public inputs | Yes, in tx logs | Yes, in tx logs (if necessary) |
| Private inputs | No | Yes, both from user and from T3N Storage (user data) |
| Programming Language | Specific (Solidity, Rust) | Flexible, any language compiling to WASM (Rust, Golang, Typescript) |
| Calling external APIs | No | Yes |
| Calling node functions | Yes, with precompiles | Yes, with WASM host functions |
| Calling decentralized Protocols | No, in EVM there are no protocols | Yes, with WASM host functions (e.g. threshold decryption, threshold ECDSA signature) |
| Execution speed | Slow. Requires block time | Fast. only limited by the threshold protocols |
| Execution logging | Yes, in tx | Yes, flexible, not revealing private information |